It’s never been more critical to protect digital assets. Learn how to have a secure data room that also protects the digital assets within it.
How Secure Data Rooms with DRM Controls Prevent Leaks
Companies that don’t utilize a secure data room for their private digital assets are at the most risk of experiencing leaks. For a business owner, the potential of lawsuits, loss of revenue, reputation, and other negative impacts caused by an unforeseen leak can be devastating.
How Leaks Can Occur Without the Use of a Data Room
There are a variety of different ways that data leaks can occur when your digital assets are shared or distributed without the use of a data room or any other protection mechanism. Some leaks are more malicious than others, but even the most innocent type of leak can be quite detrimental. Here are some examples of different types of leaks:
-
-
- An email with numerous attachments accidentally sent to the wrong person
- Email and files are inadvertently posted to a company network and a disgruntled employee decides to send the files to a competitor or leaks them to the media
- Someone's laptop with all the unprotected files downloaded ends up getting stolen
- A hacker breaks into a company's network and encrypts all the company's files with ransomware (a type of malware that threatens to leak the victim's data or perpetually block access to it unless a ransom is paid)
-
You can see how the first example is in no way malicious but detrimental depending on who the email 'accidentally' got sent to. The second example also starts off innocent enough as the person may not have realized they shouldn't have saved the files to the company's network drive, but then quickly turned malicious by a disgruntled employee. The third scenario is unfortunate but again, it could turn serious if the person who stole the laptop sold the information and files to the company's competitor or the media.
The last example is the most malicious of them all. These leak stories usually go something like this, a financial advisor sits down in a coffee shop to review an M&A deal. There’s a free Wi-fi network named after the coffee shop so he connects to it. Unfortunately, the network is a fake one fishing for victims. The hacker detects the valuable files and immediately deploys a Ransomware virus. Now the company has to either pay to get their digital assets back or risk a leak breaking the million-dollar deal.
Whether they’re innocent or malicious, security breaches can have serious consequences.
3 Reasons Why Organizations Need a Secure Data Room
Regardless of your company size, a leak of your company’s digital assets (price sheets, training manuals, financial documents, design specs, trade secrets, etc.) should be avoided at all costs. Secure data rooms make it easier and more affordable than ever to protect your confidential documents, videos, images, and audio files.
Three reasons your company should make use of a secure data room:
1. To Protect Your Digital Assets and Prevent Leaks
Your digital assets may contain your company's intellectual property, your financial information, or your trade secrets, all of which need to be protected and only shared with those authorized to view it. NDAs and contracts have likely been signed so it's imperative that this information does not get leaked to your competitors, the media, or others who shouldn’t have access.
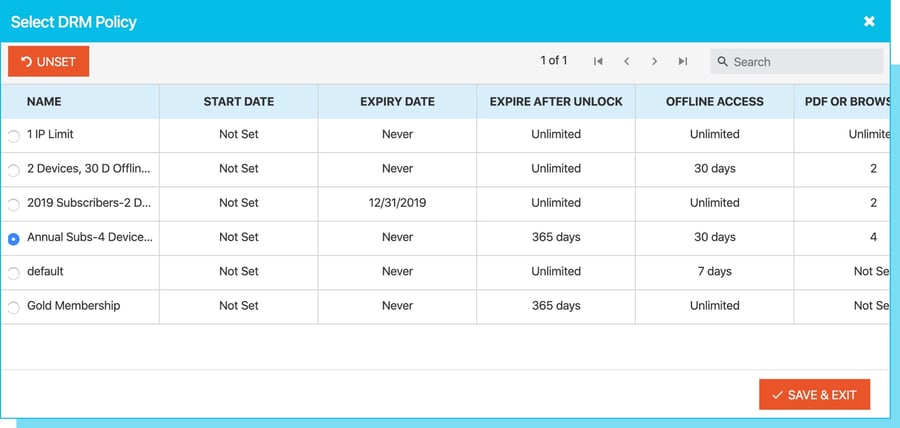
A good secure data room not only protects the room that your assets are housed in but also the individual files, including the downloadable versions of those files. It should also include various digital rights management (DRM) controls to manage the use and access of such information.
2. Simplify Your File Sharing Process
With a secure data room, your digital assets can be accessed in real-time, from anywhere. Without the need for physical copies of data, companies can deliver a better client experience.
For example, if a client is waiting on a contract for an impending merger, they can receive it instantly via a secure data room rather than waiting for it to be printed and sent in the mail. Of course, sending it via email is common in today's world, but then how do you ensure that both the email and the content is secure? What if you have numerous different files to send?
With a secure data room, you only need to send one email with one link to your secure data room. The client can then access multiple files in one central, secure location and save themselves the headache of digging through numerous emails.
3. Control & Track Your Content's Usage
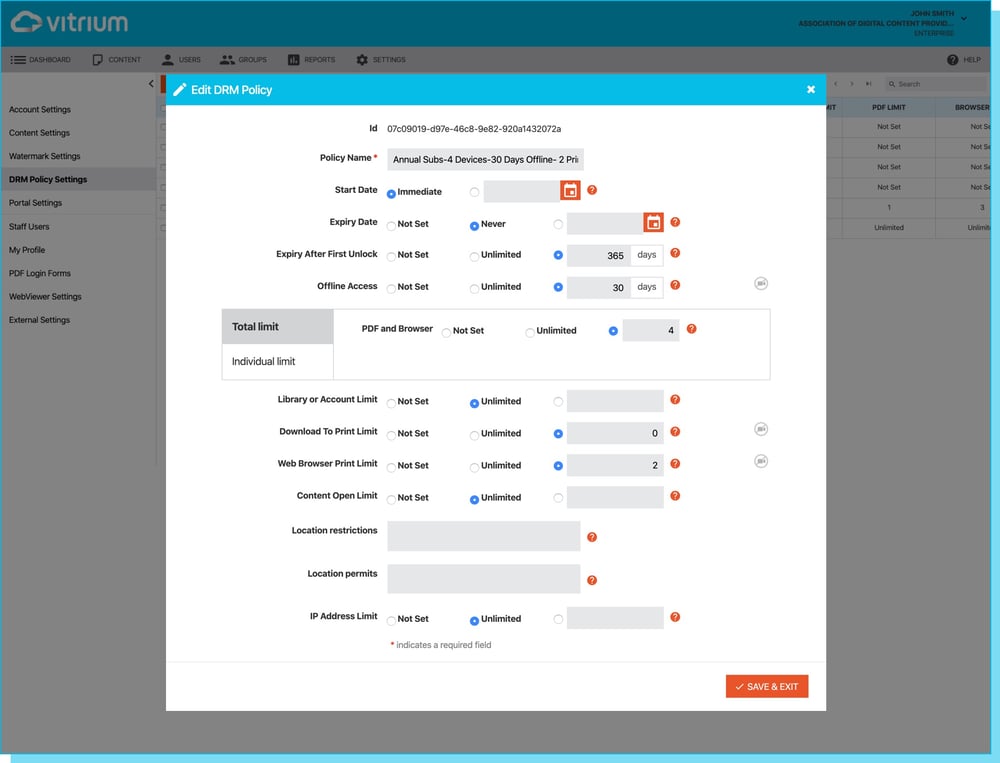
Whether you're trying to protect confidential or sensitive information, copyrighted content, or content that generates revenue for your business, content security is of utmost importance. Properly secured data rooms not only allow you to secure your content with high-grade encryption that travels with the files anywhere they go but also provide complete control over how users can access the content.
Good data rooms are armed with a variety of content control settings that include print and copy limitations for documents, view restrictions for video, custom watermarks, browser and open limits, expiry dates, and more. Even better ones will also be able to track and monitor what files are being opened or viewed, by whom, for how long, on what date and time, and even from which IP address.
Use a Secure Data Room & Mitigate Leaks With Vitrium Security
The best way to protect your digital assets and prevent leaks is by using a secure data room combined with robust digital rights management (DRM) capabilities. With Vitrium Security, you can securely share your trade secrets, sensitive documents, confidential data, and more with authorized users.
When you utilize a DRM solution, you can completely control and track every digital asset within your secure data room. With multiple layers of security, you won’t have to worry about the wrong people seeing your digital assets.
The secure data room acts as the bank, and the DRM controls are the safety deposit boxes hidden in the secure vault. Whether it’s innocent or malicious, security breaches become that much more difficult to execute.
Your digital assets are valuable. Give them the protection they deserve. Click here to learn more about our secure VDR solution with added DRM capabilities.